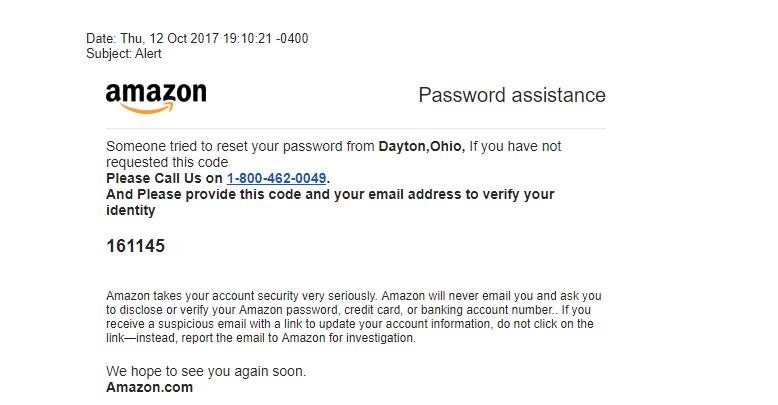
A victim of phishing from 2015, asked her bank for a refund of 3300€, which was the amount diverted by a fraud author. However, during the legal procedure, the Justice has cancelled the judgement of the local court of October 2017, which has requested to the bank of the victim to refund the corresponding amounts of the phishing operation.
The reason of this cancellation? The victim has deliberately communicated some confidential data regarding her credit card, by falling into the trap of a phishing email (the scammer has posed as the telephone operator of the victim).
This cancellation argument argues that indeed, the mail didn’t have any recipient nor sender name and that the reject or unpaid mention was inexact. Also the victim could have prevented the trap set and not communicate her banking information. Therefore, it was her responsibility, which indeed cancels the request for the stolen money refund by the bank.
The majority of phishing websites use domain names associated to an existing activity or referring to an activity, with the aim to deceive users, by inviting them to click on the links of legitimate websites. It allows to increase the likelihood of the attackers’ success.
The phishing concept is to retrieve personal data on Internet via identity theft, adapted to digital support.
If it is true that fraudulent payment online is directly caused by the victim’s negligence, yet, she didn’t communicate neither her credit card confidential code, nor the 6 digit 3D SECURE code, which was sent to her by SMS to validate the payment. The victim has blocked her credit card the same day, after the reception of two 3D secure messages.
However, in this case, the bank affirms that regularly, it has raised its customers ‘awareness and communicated with them, in order to alert them of phishing risks and warn them to never communicate their confidential banking data.
Thus, the Court of Cassation has judged that the victim acted carelessly and could have prevented to fall into the trap of the fraudster.
Cyber threats heavily rely on web users’ bad practices, as the SANS Institute confirms. The threats the most frequently encountered in companies are phishing (72% of the respondents), spywares (50%) and ransomwares (49%).
According to the American company Webroot, about 1.385.000 unique phishing websites are created each month, with an impressive peak of 2.3 million during May 2017.
Be aware that these phishing websites stay active during a very short period: between 4 and 8 hours maximum, to prevent to be followed or blacklisted.
Of course, this case reminds that vigilance remains crucial more than ever!






 These 23 and 24 January, has taken place in Lille, the 10th edition of the International Cybersecurity Forum (FIC). With 7000 participants, 240 partners and 60 represented nationalities, it is a major event in terms of cybersecurity and digital confidence, gathering all the actors in France and in Europe.
These 23 and 24 January, has taken place in Lille, the 10th edition of the International Cybersecurity Forum (FIC). With 7000 participants, 240 partners and 60 represented nationalities, it is a major event in terms of cybersecurity and digital confidence, gathering all the actors in France and in Europe.