On October 9, Apple revealed to the CA/Browser Forum that it had posted a draft ballot for comment on GitHub regarding two important SSL/TLS certificate lifetime events:
- Gradually reduce the maximum duration of public SSL/TLS certificates to 45 days by 2027;
- Gradually reduce the reuse period for DCV challenges to 10 days by 2027.
In March 2023, in its “Moving Forward, Together” roadmap, Google announced its intention to offer the CA/B Forum a reduction on the maximum possible validity period for public TLS certificates going from 398 days to 90 days. Since this announcement, the market has been feverishly awaiting for Google’s confirmation but most of all, for the implementation’s timetable… without success. For its part, Mozilla announced, a few weeks ago, its intention to follow Google’s lead on its Firefox browser, without adding any further detail.
Apple ultimately took the first step last week, announcing on October 9th its intention to both reduce the lifetime of certificates to 45 days (when the entire market was expecting 90 days) and to limit the duration of the DCV challenge to 10 days, according to the schedule below. A true bombshell:
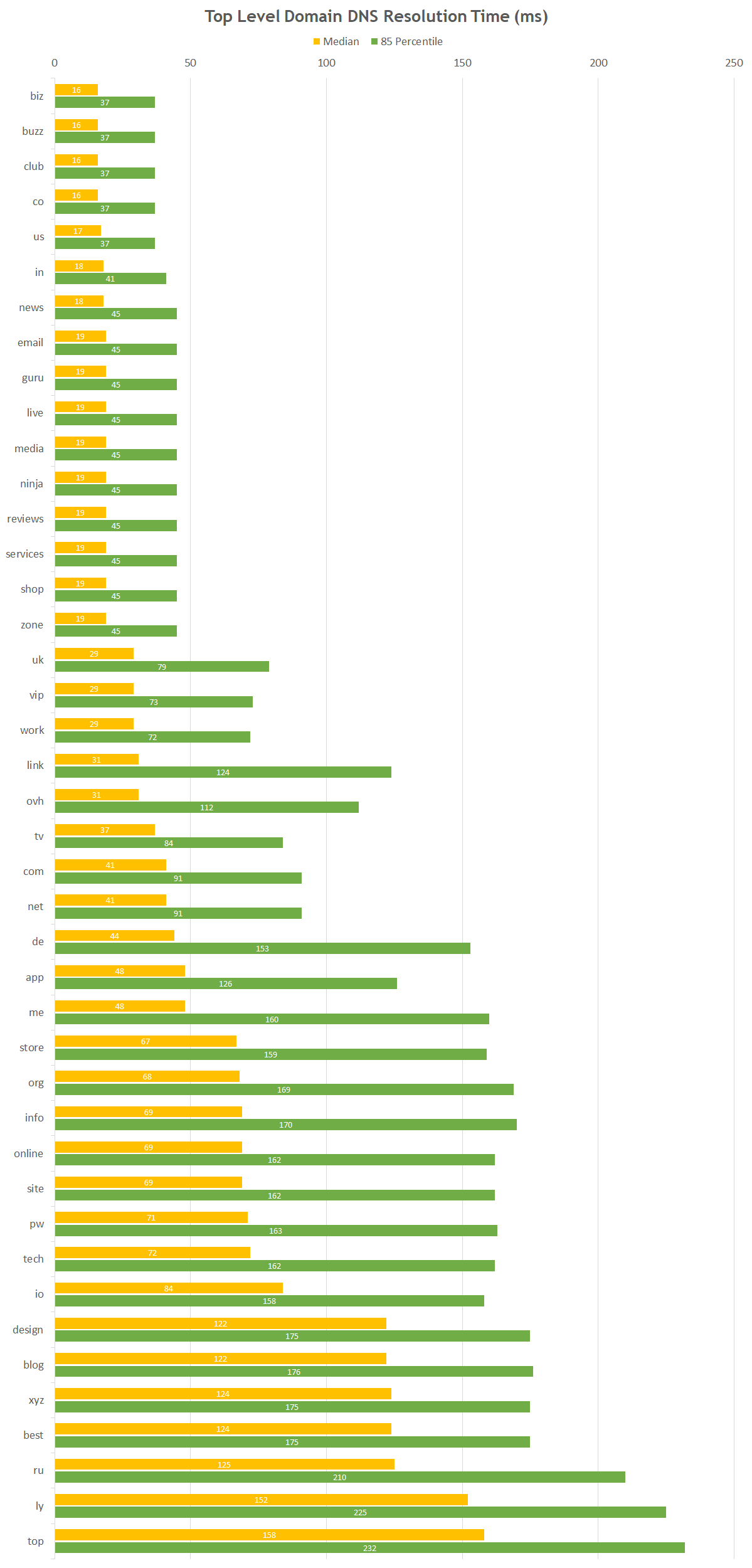
Sep-15-2025 => certificates and DCV validation times reduced to 200 days
Sep-15-2026 => certificates and DCV validation times reduced to 100 days
Apr-15-2027 => certificates and DCV validation times reduced to 45 days
Sep-15-2027 => DCV Validation time: 10 days
Information on the background and analysis of this announcement, the expected outcomes and how to prepare for them will undoubtedly be useful:
Context and Analysis:
At this stage, the publication is likely to be commented by market players prior to the formal drafting of the ballot within the CA/B Forum, which itself will be voted on by its members: the Internet browser publishers on the one hand (Google, Mozilla, Apple and Microsoft…) and the Certification Authorities on the other. Amendments are bound to be made, but the general idea remains and the machine is up and running.
Indeed, software publishers are all aligned on the need to reduce the lifetime of certificates, and among Certification Authorities, Sectigo, one of the major players in the certificate industry, is already supporting the initiative. It is likely that things will move rapidly from now on, with few comments and a ballot drafted in the coming weeks or months. We will then know more about the confirmation of the durations and timetable, and will of course make sure to keep you informed.
Expected Outcomes:
- Certificate lifetime: whether 90 days, 45 days or even less, this reduction is no longer a surprise, and will have a major impact on public certificate portfolio. The certificates can no longer be managed manually. The market has begun its transition to automation, notably through CLMs (Certificate Lifecycle Managers). The issue at stake for companies and organizations will be to rely on partners who can offer as many interconnections as possible between Organizations, Certification Authorities and CLMs.
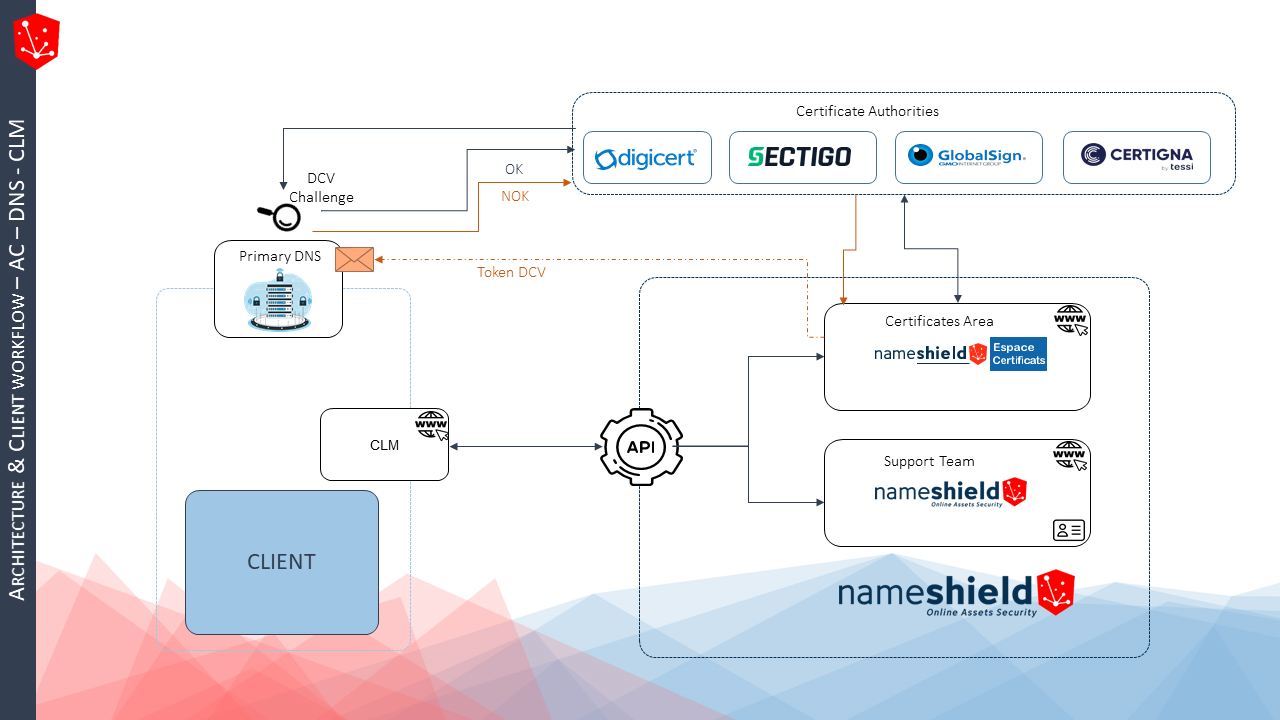
- DCV challenge duration: Reducing the duration of the DCV challenge to 10 days, if validated, would have a considerable impact, perhaps even more so than reducing the lifetime of certificates. Up until now, the industry has pre-validated domain names for 398 days, using the DCV challenge only once. Apple’s announcement would thus force the use of a DCV challenge for virtually all orders, which would be a major paradigm shift and would involve interconnections with an additional brick in the ecosystem: the DNS. The DCV (Domain Control Validation) challenge involves intervening in the zone of the domain name(s) listed in the certificate, ideally instantaneously, to validate it.
- Organization authentication duration: Apple has not announced anything on the subject of the validity period of organization authentication for OV certificates, which is currently 825 days. However, rumors are circulating that this may be reduced to 398 days or even 365 days.
How to be ready:
The key to successful certificates management lies in automation. A 45 days certificate lifetime represents 9 interventions per year per certificate. Manual management thus becomes utopian. We therefore need to rely on:
- Certificate Provider/Certification Authority (CA): a trusted partner who will support through your organizational and domain authentication issues. Service level is key to good management. A multi-CA partner is thus recommended to limit dependence on a single CA, as in the case of Entrust’s recent setbacks.
- Registrar / Primary DNS: mastering the primary DNS of domain names listed in certificates will become the key to delivery. Each time a certificate is issued, a TXT or CNAME will be installed on the zone(s) in question. An interconnection between the CA and the DNS is vital.
- CLM editor: the CLM’s role is to inventory the certificate portfolio, to define certificate portfolio management rules and automate the entire process of orders, from the generation of CSRs to the deployment of certificates on servers. To function properly, the CLM relies on connectors with CAs or certificate suppliers.
Getting ready thus means identifying the most suitable solution, based on these three dimensions, and undertaking this analysis to understand the impacts in terms of process, technology, and budget – in an ideal world – before the end of the first half of 2025.
Nameshield’s approach:
Nameshield holds a unique position in the market as a registrar and supplier of multi-AC certificates. For over 10 years, we have been managing the day-to-day issues associated with authenticating organizations and domains using certificates. On the one hand, we have a privileged relationship with the biggest CAs on the market (Digicert, Sectigo, GlobalSign), and on the other, we master the DNS brick for DCV validation. As a result, we can issue public certificates almost instantaneously. Last but not least, Nameshield has connectors with the major players in the CLM market, allowing you to ensure a comprehensive connection between the various components involved in certificate management. This way, we can support you in anticipating all the issues mentioned above.
For more information, please contact our Sales team or our Certificates team.
Crédit image : Nameshield with storyset.com