The slamming is a fraud aiming to deceive companies in order to sell by emails unsolicited services for domain names.
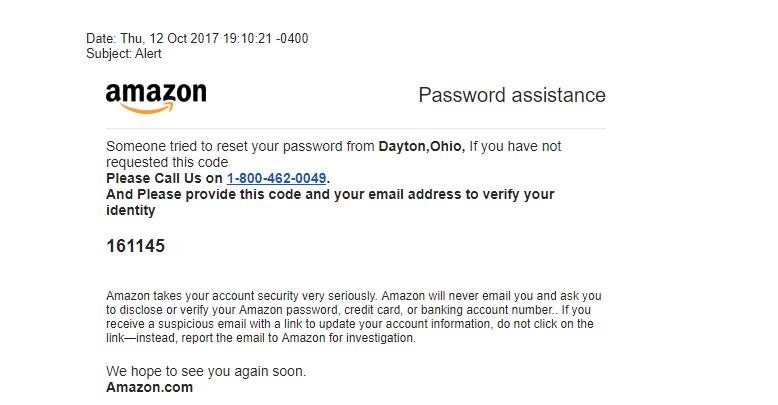
These slamming attempts are easily recognizable and play on their contacts lack of knowledge in some cases. The slammers propose services that you didn’t solicit with your official registrar (registration, whois’update, owner or registrar transfer…) at high prices. These emails are sources of anxiety and lead you to take a quick decision.
For example, a standard slamming email would encourage you to register domain names in emergency because a third party would have done a domain names’ registration request using exactly your company name or your lead product, identically (as if by chance). They recommend you to register them without delay to prevent any cybersquatting. Obviously, the “fake registrar”, in its great magnanimity has put on standby the domain name registration order for the good of the company…
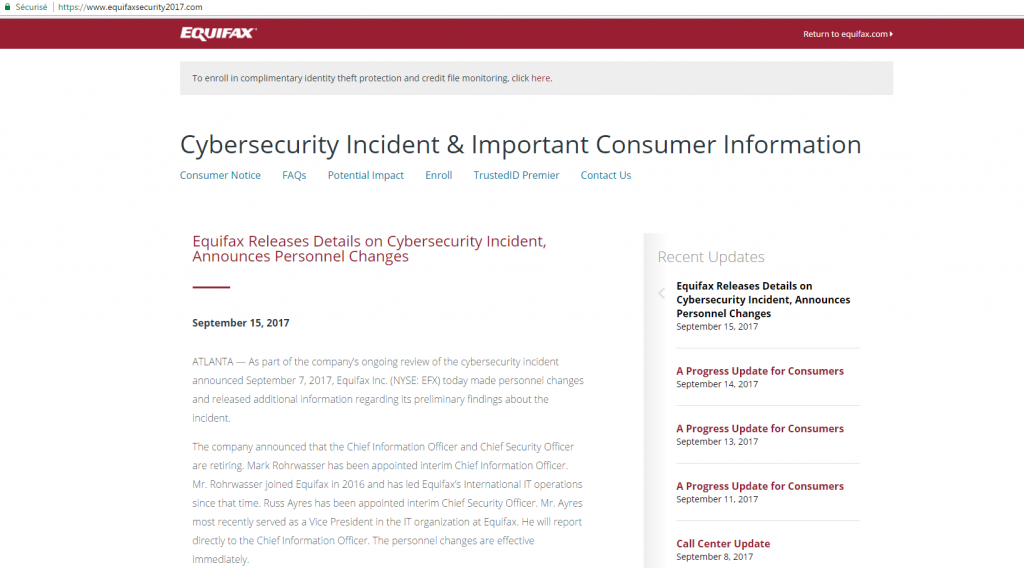
Warning, the slammer uses visual references and the right technical vocabulary, misleading that way the company. They can also make reference or put the logo of some registries or actors of the Internet environment in order to give credibility to their speech.
What to do if you have any doubts?
Forward your emails to Nameshield, which will confirm you if these mails are fraudulent.
We recommend a management of your domain names centralized and managed by a person informed of the operations associated to domain names. Don’t take any decision in a hurry. You can also make a whois to verify the sender’s identity and the existence of the “registrar” company. You will then notice that most of the domain names used for slamming campaigns have been recently registered and that the companies holding the names are unrelated to the registration office activity.
Be careful, your domain names are intangible assets to protect, secure and value.
Nameshield assists you on a daily basis, in the management of your domain names portfolio, your digital brands protection and the risks management on the web.