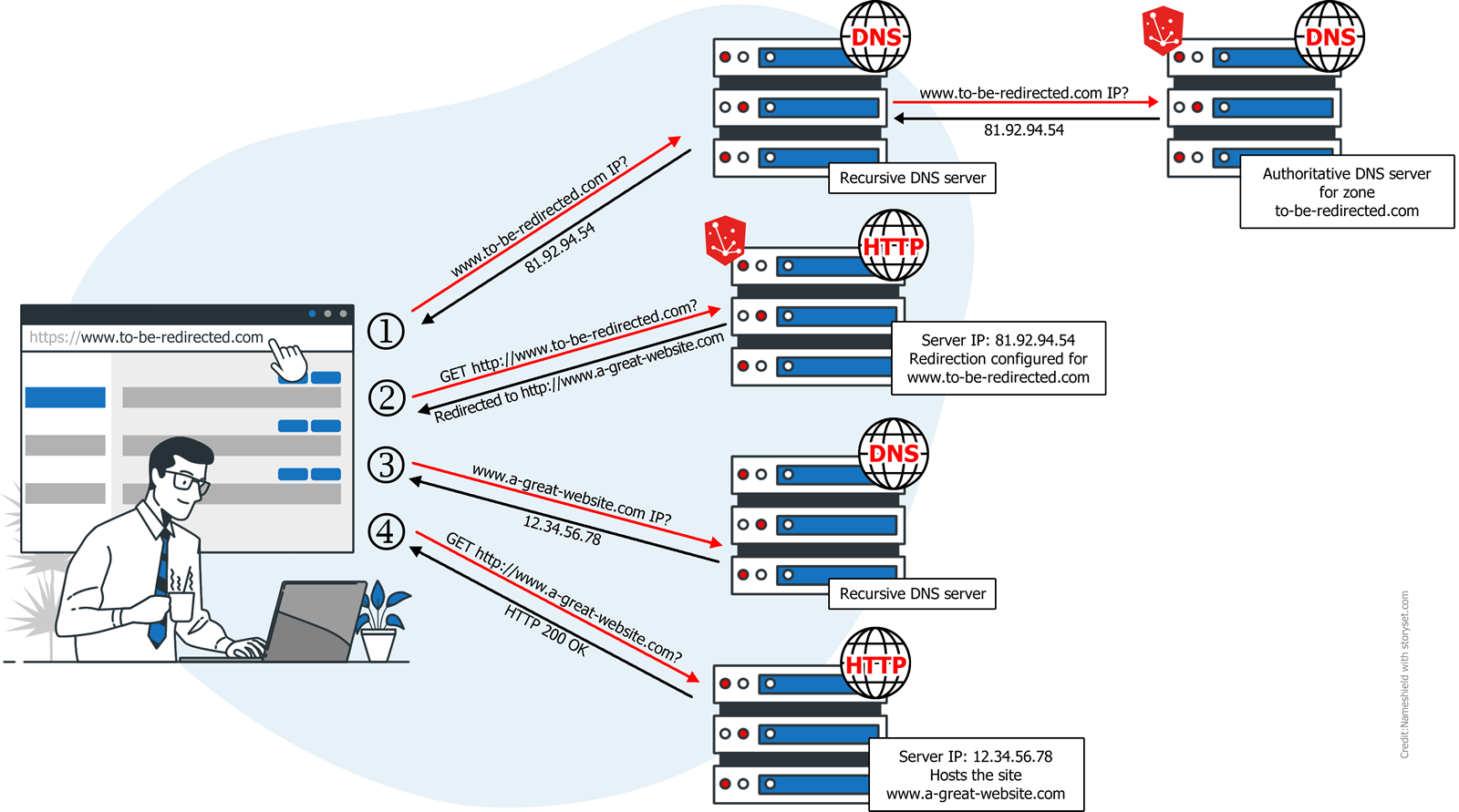
Candidate in March 2020 and then in March 2021, the city of Cancun finally had to wait until March 2023 and the end of the COVID pandemic to see a new edition of an ICANN summit in person. 2023, a very important year for the organisation. It will indeed celebrate its 25 years of existence while it is going through a risky period with an interim presidency after the resignation of its former President on 22 December 2022.
Two women at the head of ICANN
Sally Costerton from the UK, who has been Vice President of Global Stakeholder Engagement (GSE) in charge of stakeholder engagement and awareness of ICANN and its mission worldwide since 2012, has been appointed interim Chief Executive Officer of ICANN following the departure of Goran Marby at the end of 2022. She is supported by Tripti Sinha who serves as ICANN’s Board Chair. Tripti is also Associate Vice President and Chief Technology Officer at the University of Maryland, in the Information Technology Division. This is the first time ICANN has had two women leaders. However, the situation echoes the creation of ICANN. As it was recalled at the opening ceremony, in 1998, when the US government gave ICANN the task of managing the DNS addressing system, a woman also held the position of Chair of the Board. This was Esther Dyson.
While leadership interims are rare at ICANN, this situation led to the organisation of a special session called “The Future of ICANN and the Next President and CEO”. A session where participants would have expected to interact with the new Board. This was not the case, as this session was like a kind of open mic without a direct interlocutor to express expectations towards the new Management of the organisation.
An interim presidency for a governance organisation also means a risky period, especially as there is no shortage of issues to address and the geopolitical context is tending towards increased fragmentation. However, although we do not know how long the interim presidency will last, Sally Costerton quickly made her mark at the start of the summit, when she declared, among other things, “I do not know everything, but I can rely on experts“. These words were reassuring and showed a pragmatic approach.
Transparency tested by experience
ICANN is a well-established organisation, as it has been holding summits for 25 years. The trend in recent years has been for the Supporting Organisations (SOs) and Advisory Committees (ACs) that make up the organisation to move towards greater transparency by opening up almost all their sessions to the participants. The most significant transformation has been in the GAC, the body representing governments, whose sessions were closed for many years before being fully open to all participants. This is an opportunity to salute the work of Manal Ismail, who after nearly six years at the head of the GAC is leaving her place to the Paraguayan Nicolas Caballero. A global tendency, therefore, of a nature to generate confidence, a key value to respond to the more and more numerous detractors of the ICANN governance mode.
But this tendency was reversed during this summit because many sessions were closed, “Closed sessions” to which even some affiliated participants could not have access neither in face-to-face nor in remote. Some of the participants were very upset and did not fail to point this out during the traditional Public Forum which usually closes the week of meetings.
Progress at a forced march?
The consensual approach, typical of ICANN, is both a strength for federating players around new obligations that are adopted, but also a weakness because it considerably slows down the progress of important work.
A striking example is the DNS abuse. Malicious use is indeed a real problem given the damage suffered by the affected Internet users. The GAC did not fail to recall this once again during a session where external experts were invited, such as a representative of the Federal Bureau of Investigation, the FBI. The latter indicated that in the United States, in 2022, more than 800,000 domain names were the subject of complaints causing losses of more than 10 billion US dollars. While the topic of DNS abuse has been a recurring theme at every ICANN summit over the years, it is clear that the consensus has shown its limits. Stakeholders in the GNSO, the generic name policy body, have never been able to agree on a way forward, whether it be a Policy Development Process or contract negotiations to revise stakeholder contracts with ICANN. After recent consultations with stakeholders, the GNSO finally decided on the second option, and the least we can say is that at ICANN76, the will was to reach a result quickly. An amendment to the registry and registrar contracts is being drafted and is expected to be presented in June and voted on by the parties concerned in October.
The GNSO intends to build on the momentum of another contract amendment being voted on by stakeholders: an “RDAP” amendment. RDAP is an alternative protocol to Whois that provides access to domain names registration data. The outcome of the votes and thus the adoption of these contract revisions remained uncertain at the end of the ICANN summit as different thresholds of participation and favourable votes must be reached.
Partial adoption of recommendations for future rounds of new gTLDs
Another issue that some would like to see move forward more quickly is that of future rounds of new generic extensions. Indeed, the last window for applications for generic extensions dates back to January 2012. Since then, a policy development process has been conducted since 2015 to define a set of recommendations for the holding of new application windows. The Final report of this process was submitted to the ICANN Board in February 2021. In the autumn of 2021, ICANN surprised the community by announcing a scoping phase, an ODP (Operational Design Phase), which ultimately lasted until the beginning of this year. The board had not yet decided on the Final report of recommendations, a prerequisite to be able to start the implementation work of the recommendations. So the new interim president of ICANN was also very much expected on this subject.
And she quickly warned that the time was also for action on this subject: “You will see that things will be clarified” (editor’s note: on the next series of generic extensions), she declared during a session during the week. At the end of the week, at a Board meeting, 98 recommendations from the policy development process were adopted, with a further 38 put on hold as requiring further information. An implementation plan is also expected with a deadline set to 1st of August with a focus on internationalized domain names and extensions that ICANN organisation wants to focus on in future rounds and the need to clarify whether closed generic extensions will be offered.
Comments from NAMESHIELD
We can regret a return to a certain opacity in the decision making during ICANN76 where no less than 25 closed sessions were held. Nevertheless, this is perhaps where the progress made on subjects that were not progressing well came from, such as DNS abuse, a very important subject for NAMESHIELD, which offers several solutions to defend your online assets, and the holding of a forthcoming series of new generic extensions, where NAMESHIELD experts can also accompany you.
The other question was how the new interim ICANN President Sally Costerton, would handle her new role in a risky period for ICANN whose model is also increasingly challenged by States, international organisations and even technological alternatives. On this point, the new president appeared to be proactive, joining words to deeds, as on the subject of further series of new generic extensions. Sally Costerton seems to have already started to trace her way towards a full term CEO role for the organisation.
Image source : ICANN’s website