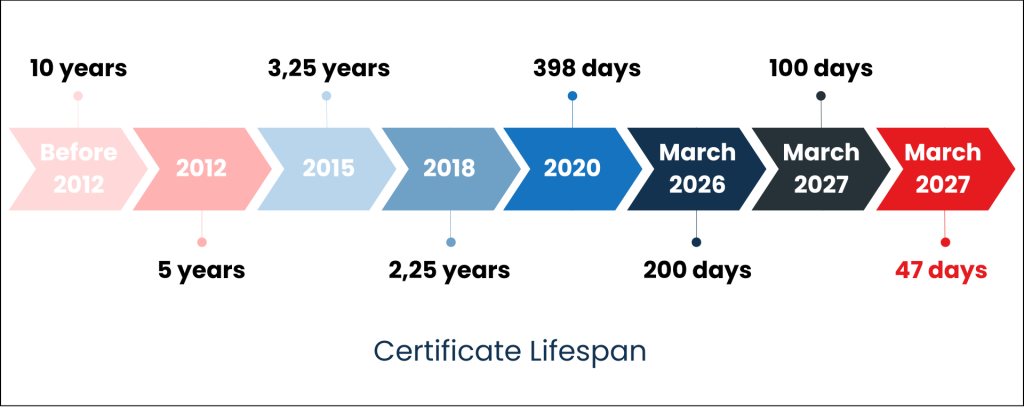
On 9 October 2024, Apple announced at the CA/B Forum (Certification Authority Browser Forum) its intention to reduce the maximum duration of public SSL/TLS certificates to 45 days by 2027, as well as to reduce the DCV challenge reuse period to 10 days by 2027.
This request was then discussed and amended six months later, again by Apple, which proposed a change to the initial schedule with a reduced certificate duration of 47 days for SSL/TLS certificates and a DCV challenge validation period of 10 days from 15 March 2028.
This measure officially comes into force following the CA/B Forum vote in April 2025, which adopted a new implementation schedule, officially reducing the validity of certificates to 47 days and thus promoting automation for the proper management of these certificates.
- Until 15 March 2026, the maximum TLS certificate lifetime will remain at 398 days.
- From 15 March 2026, the maximum TLS certificate lifetime will be 200 days.
- From 15 March 2027, it will be reduced to 100 days.
- And from 15 March 2029, the maximum TLS certificate lifetime will be reduced to 47 days.
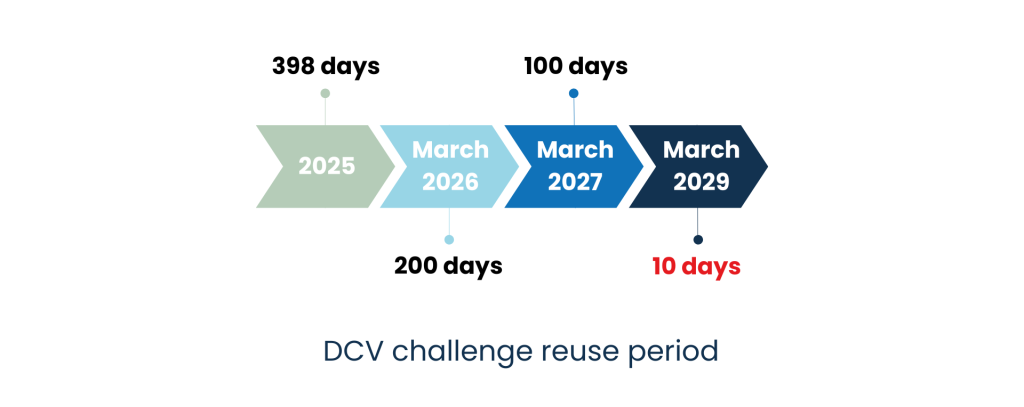
At the same time, the reuse periods for Domain Control Validation (DCV challenge), which involve intervening in the domain name zone listed in the certificate to validate it, will be aligned with the certificate schedule, reaching 10 days in 2029.
- Until 15 March 2026, the maximum period during which domain validation information can be reused is 398 days.
- From 15 March 2026 onwards, the maximum period during which domain validation information can be reused is 200 days.
- From 15 March 2027 onwards, the maximum period during which domain validation information can be reused is 100 days.
- From 15 March 2029 onwards, the maximum period during which domain validation information can be reused is 10 days.
Faced with these major changes coming in 2026, it is essential for businesses to prepare
The CA/B Forum’s initiative will gradually transform the digital certificate security landscape. The validity period of SSL/TLS certificates will be reduced, accompanied by stricter DCV challenge validation rules. The key to effective certificate management in the future will therefore lie in automation. With certificates valid for 47 days in 2029, that means nine interventions per year per certificate, making manual management unfeasible. It will therefore be necessary to rely on the following services/software:
- Certificate provider/Certification Authority (CA): a trusted partner who will assist you with organization and domain authentication issues. The level of service is key to effective management. A multi-CA partner is recommended to limit dependence on a single CA, as demonstrated by the recent difficulties experienced by Entrust.
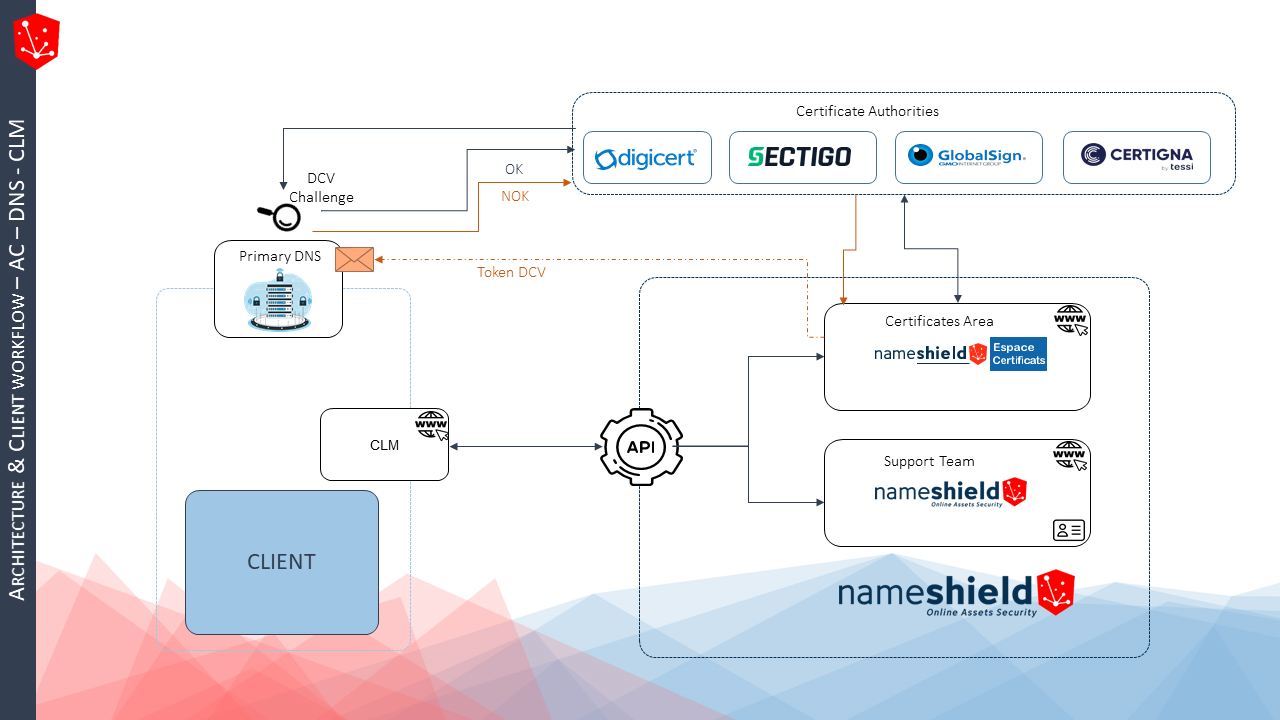
- Registrar/Primary DNS: controlling the primary DNS of the domain names listed in the certificates will become key to delivery. Each certificate issue will result in the installation of a TXT or CNAME on the zone(s) concerned. Having an interconnection between the CA and the DNS is essential.
- CLM editor: the CLM is responsible for inventorying the certificate pool, defining pool management rules, and ensuring complete automation of the ordering process, from CSR generation to certificate deployment on servers. To function, it relies on connectors with CAs or certificate providers.
Preparing therefore means identifying the solutions that suit you best in these three areas and starting to think about the impact on processes, technology and budget, so that you are ideally prepared for the first half of 2026.
Nameshield, an ally to help you manage these changes
Nameshield occupies a unique position in the market as both a registrar and a provider of multi-CA certificates. For over 10 years and on a daily basis, we have been managing all issues related to organization and domain authentication linked to certificates, thanks to our privileged relationship with the largest CAs on the market (Digicert, Sectigo, GlobalSign) and our expertise in DNS for DCV challenge validation. As a result, we issue public certificates almost instantly. Finally, regarding the CLM component, Nameshield has connectors with the largest players on the market to enable you to ensure a complete connection between the various components related to certificate management. We therefore support you in anticipating all the issues mentioned above.
If you have any further questions, you can contact Nameshield directly here.