Act 1: Denial (and Anger)
The brand, a forbidden territory. Everything is played out by attacks, complaints, courts. A ruthless world. Since the 23rd of June 1857 and the creation of the first system of trademarks by France, it is possible to benefit from an exclusive right of use for a term on different applications. Otherwise the law is coming. The arrival of the Internet will shake up this foundation.
If one remembers the Milka conflict with Kraft foods, which led to the famous opposition between Milka Budimir, a seamstress in Bourg-lès-Valence, and the American giant Kraft Foods about the domain name milka.fr, we can keep in mind the case of many domain names holders who succeeded in winning attacks against those bigger than them.
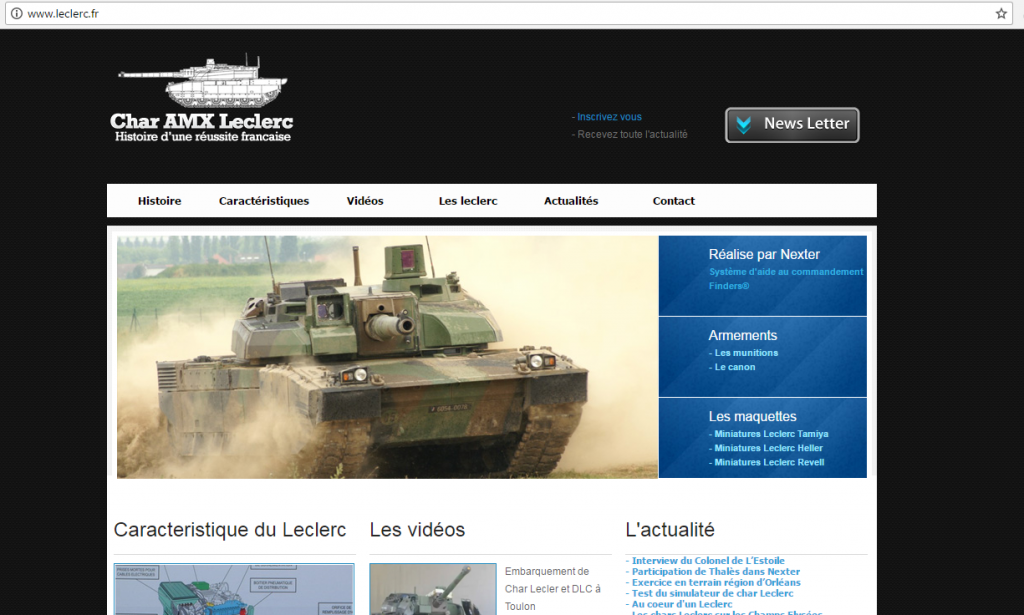
The expression of David vs Goliath is illustrated in France with leclerc.fr, domain name registered by a fan of the Leclerc tank. In spite of an attempt at recovery of SYRELI type, the tradesmen never succeeded in obtaining this famous domain name. For posterity, the justification of the individual will be retained in his argument: “… in life there are not only shopping centers and consumption, France is above all, a country of history, a strong history of which we can be proud!”
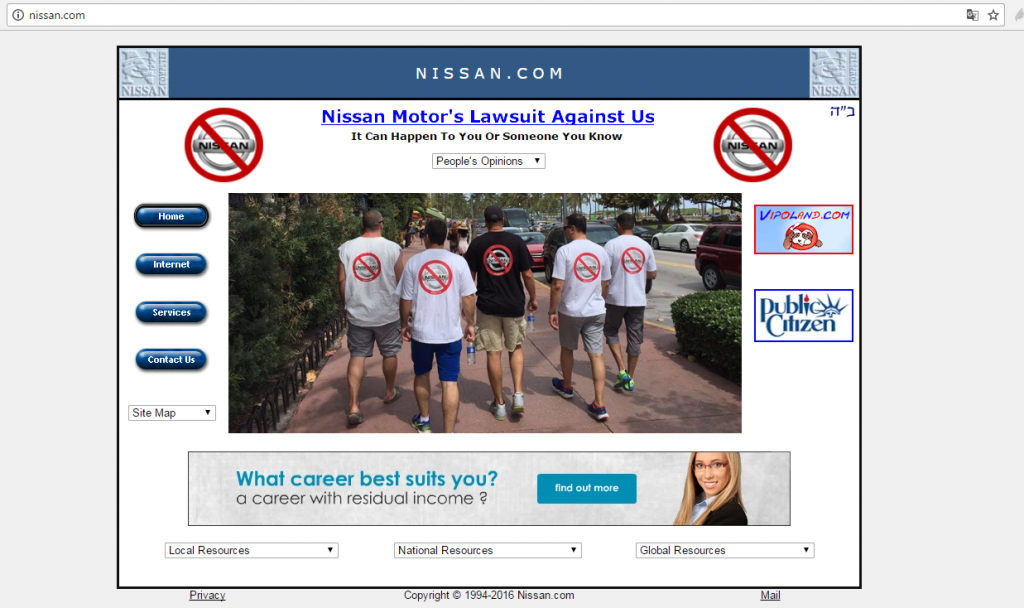
In the United States, the case of Nissan Computers is interesting. The little known IT company was registered after the name of its owner, Uzi Nissan. The eponymous Japanese company Nissan Motors evidently pouted at the deposit of nissan.com and tried to recover the domain name in question. Despite an incessant media campaign and numerous attacks, today nissan.com remains the property of Nissan Computers. Nissan Motors now uses nissanusa.com for its US business. In this case, the Nissan.com website only reflects Nissan Computers’ computer sales activity. We can instead find a strong attack against Nissan Motors. A bad buzz in action!
What can we keep in mind through these two experiences? A relatively interesting bone marrow: the domain name, this intangible asset representing the image of a company, has not been sufficiently monitored by multinationals.