Act 2: Expression
We left off on the time when the brands did not feel the Internet revolution, the techniques evolving and the registered domain names. (Read act 1: Denial (and anger))
The example of McDonald’s is interesting. In 1994, Wired, an American magazine created a year earlier, communicates about the case of mcdonalds.com. Joshua Quittner, a journalist at Newsday, contacted McDonald’s and asked if they would be interested in registering mcdonalds.com. There was little to no answer. He registers the name, contacts McDonald’s which does not answer. Then he publishes his article on Wired, putting the contact address ronald@mcdonalds.com.
McDonald’s complains and Quittner asks for a donation for charities: it will be 3500USD for the computer equipment of a school in New York.

In analogy, we can remember when a Russian worker asked for a gift from Vladimir Putin, who could not refuse in front to the camera. Putin offered him his watch worth a year’s salary.
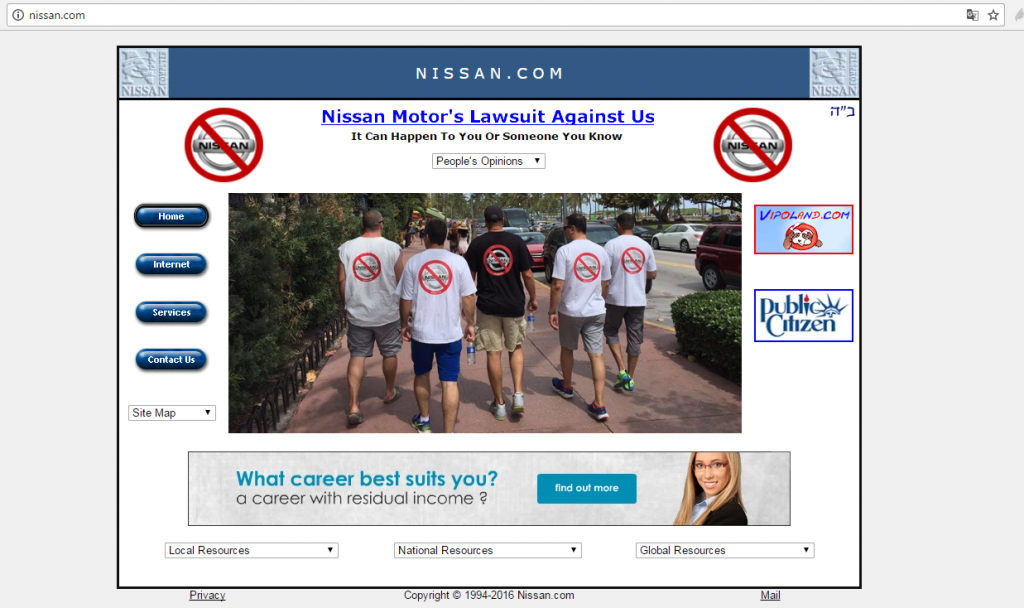
The virulent attacks of trademarks are legion in order to recover the domain names from little jokers, some of them could be part of the company, such was the case for mtv.com.
Brands federate among themselves, contact ICANN to develop simplified procedures, even if, according to the famous trademark dilemna, the American organization had known the risk of cybersquatting for a long time.
On the side of lawyers, training courses are launched on each side of the Atlantic and the UDRP, SYRELI, URS and others, are created in order to defend the digital territories.
France, known for a long time as a country supporter of trademarks, will not remain passive and is today, the second country in the world in the disputes resolutions concerning domain names.
Thus, in the virtual territory, and in contrast to the reality, the police is financed by trademarks. The holders of a territory, similar to countries, are doing nothing or almost nothing: recovering a .Fr can be possible using a SYRELI procedure, while for our friends from the outside of Rhine, no alternative procedure exists: to apply for its .DE, it is the court or nothing.
Nevertheless, an economy of defense of brands is organized and thus, an ecosystem is developed.
Everything seems to be going well, until the arrival of the new extensions, as called in the field, the first round…