On October 29, 1969 UCLA sends the very first e-message to Stanford Research Institute through Arpanet network (Advanced Research Projects Agency Network) laying the foundation for today’s networked world.
Arpanet, the Internet’s precursor
Arpanet is the first data transfer network developed by the Advanced Research Projects Agency (ARPA) which belonged to the U.S. Defense Department.
The first Arpanet node was set up at UCLA on August 30, 1969, the second node, at the Stanford Research Institute, was set up on October 1st 1969. The first message was sent between the two institutions on October 29 1969 by the UCLA computer science professor Leonard Kleinrock who wished to send the word “login” but the system crashed so only two letters, “l” and “o”, were transmitted, the complete word will only be transmitted 1 hour later.
Arpanet connected some universities and research institutes: first, UCLA and Stanford Research Institute, followed by UC Santa Barbara and the University of Utah. At the end of 1969, Arpanet counted 4 nodes, in 1971, 23 nodes were created and 111 nodes in 1977.
In 1983, Arpanet has been divided in two networks: one military, the MILnet (Military Network) and the other academic, the NSFnet.
On January 1st 1983, the name “Internet” already in use to define all of Arpanet, became official.
World Wide Web turns 30 years old
In 1989, Tim Berners-Lee, a researcher working for the CERN, proposed a hypertext system working on the Internet. This system was originally developed for scientists working in universities and institutes around the world, so they could instantly share information. His vision of universal connectivity became the World Wide Web, which sent Internet usage skyrocketing.
In 1993, Mosaic, the first popular web browser was created by Marc Andreessen and Eric J.Bina, two students of the National Center for Supercomputing Applications (NCSA) of the University of Illinois. It was not the first graphical web browser but Mosaic was particularly fast and allowed the users to display images inside web pages instead of displaying images in a separate window, which has given it some popularity and contributed to increase the World Wide Web’s popularity.
Internet Protocol – From IPv4 to IPv6
The Internet Protocol (IP) is a set of communication protocols of IT networks developed to be used on the Internet. IP protocols allow a unique addressing service for all connected devices.
IPv4 the first major version was invented in the 70’s and introduced to the public in 1981. It is still the dominant protocol of the Internet today. Twenty years ago, the IETF (Internet Engineering Task Force) started predicting the depletion of IPv4 addresses and began working to create a new version of the Internet Protocol: IPv6.
IPv4 uses a 32-bit addressing scheme to support 4.3 billion devices, while IPv6 possesses a much larger address space. Indeed, IPv6 uses a 128-bit address allowing 3.4 x 1038 possible addresses.
DNS – Domain Name System
At the request of the Advanced Research Projects Agency of the U.S. Defense Department, the DNS (Domain Name System) was invented in 1983 by Jon Postel and Paul Mockapetris, in order to associate complex IP addresses with humanly understandable and easy-to-remember names. Thus a logical address, the domain name, is associated to a physical address, the IP address. The domain name and IP address are unique.
In 1998, is created ICANN (Internet Corporation for Assigned Names and Numbers), the regulatory authority of the Internet. Its main purpose is to allocate the Internet protocol addresses spaces, to attribute the protocol identifier (IP), to manage the domain name system of top level for generic codes (gTLD), to assign the country codes (ccTLD), and to carry out the functions of the root servers’ system management.
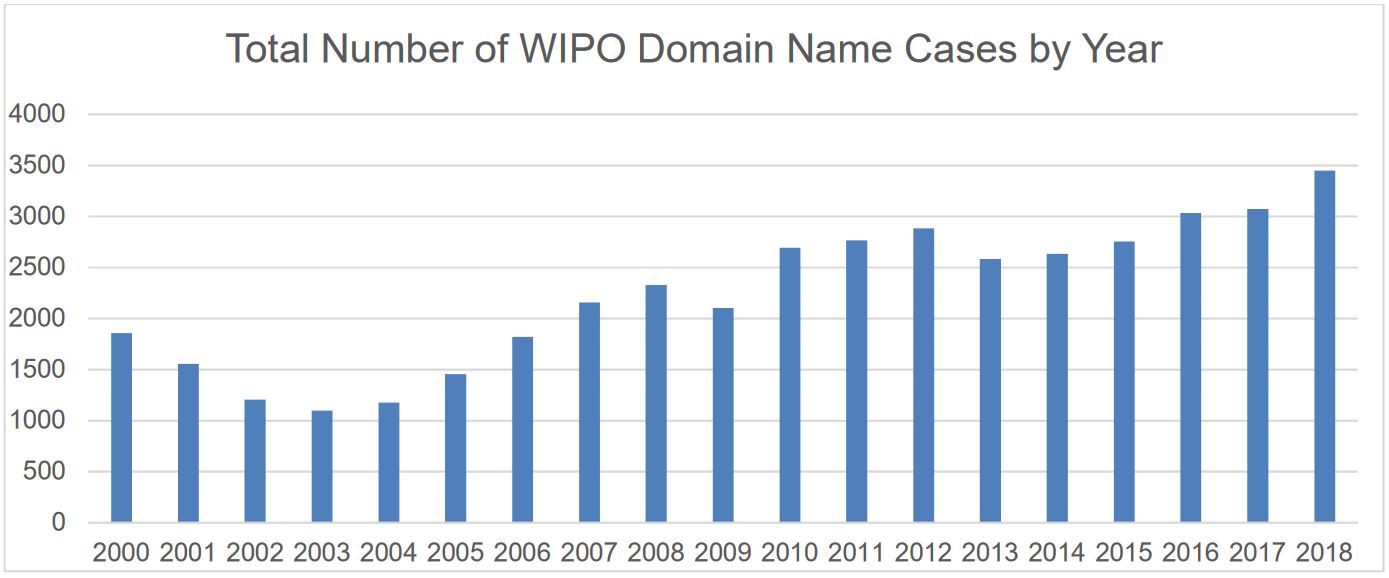
With 351.8 million domain names registrations in the first quarter of 2019, domain names registrations continue to climb, but with the increase of the number of threats aiming the DNS at the same time.
The emergence of cyber threats
Considered as one of the first cyberattacks and certainly the first to attract the media’s attention, the Morris Worm was launched in 1988 by a student of the Cornell University, Robert Tappan Morris. Originally, the malware developed by the student didn’t have for purpose to cause damage but simply to estimate the extent of the Internet. However this worm affected about 60 000 computers estimated connected to the Internet and the cost of the damages was about 100 000 to 10 million dollars. This event marks the turning point in the field of online security.
Today, cyberattacks are abundant, frequent and more and more sophisticated. The evolution of techniques and the arrival of new technologies make cyberattacks increasingly complex and offer new opportunities to attackers.
There are various types of cyberattack like attacks aiming the DNS: DDoS, DNS cache poisoning, DNS spoofing, Man in the Middle… (In 2019, according to IDC – International Data Corporation, 82% of companies worldwide have faced a DNS attack over the past year) or attacks directly aiming users and having for purpose to obtain confidential information to steal an identity (phishing).
The consequences for victimized companies can be significant. For example, today the cost of a data breach is 3.92 million dollars on average according to IBM Security, this cost has risen 12% over the past five years.
An IP traffic estimated in 2022 more important than the one generated from 1984 to 2016
With more than 5 billion Google searches made every day, e-commerce continuing to thrive, social media growing in popularity and the increasing number of connected objects, the traffic volume on the Internet has risen considerably.
Indeed, in 1974, daily traffic on the Internet surpassed 3 million packets per day. According to a Cisco’s research in 2017, the global IP traffic reached 122 exabytes per month, the company estimates that this volume should reach 396 exabytes by 2022.
“The size and complexity of the Internet continues to grow in ways that many could not have imagined. Since we first started the VNI Forecast in 2005, traffic has increased 56-fold, amassing a 36% CAGR (Compound Annual Growth Rate) with more people, devices and applications accessing IP networks” said Jonathan Davidson, senior vice president and general manager of Service Provider Business at Cisco.
Today, 50 years after the birth of the Internet’s ancestor, Arpanet, there are more Internet connected devices than people in the world. In 2022, the web users will represent 60% of the world’s population and more than 28 billion devices will connect to the Internet.