Summary
The DNS, the Domain Name System, is a service at the heart of how the Internet operates. It is fundamental to the functioning of many services such as websites, mail servers, VoIP telephony and many others.
For more than 30 years, many extensions and functionalities have been added to the DNS, which technically translates into an increase in the complexity of the infrastructure.
The Blockchain technology could be a considerable evolution for DNS, bringing several advantages and new functionalities.
—
The DNS, a fundamental service
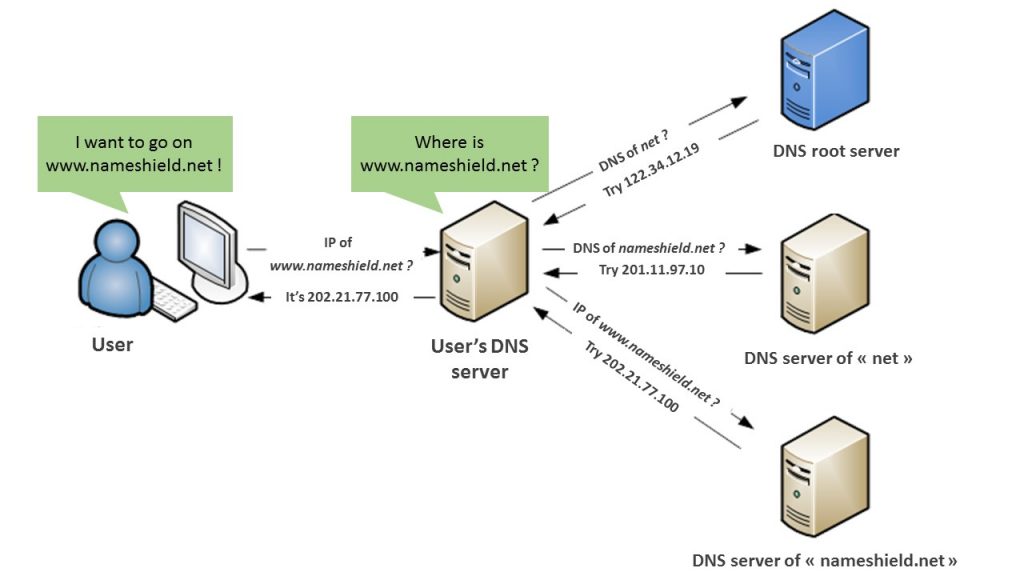
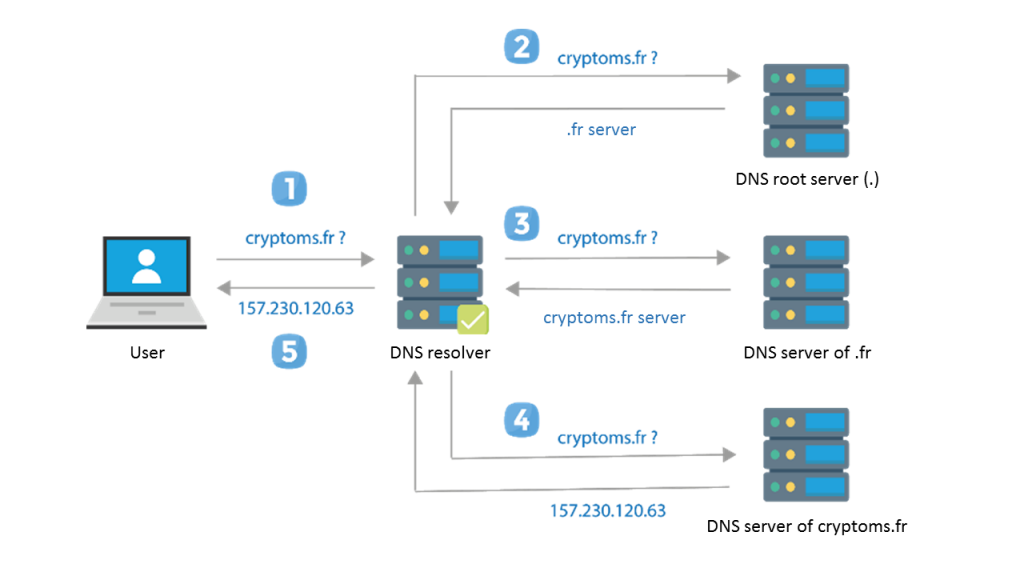
The DNS, the Domain Name System, is a service at the heart of how the Internet operates. It functions as a public directory that associates domain names with resources on the Internet, such as IP addresses. When a user enters an address in his browser, a DNS server translates this humanly understandable address into an IP address that is understandable by computers and networks. This is DNS resolution.
This system, created in 1983, is fundamental to the functioning of many services such as websites, mail servers, VoIP telephony and many others. It is constantly evolving to meet ever-increasing needs in terms of functionality and security. Indeed, the DNS must guarantee:
- Availability: an unavailability of the DNS service would result in a service disruption.
- Integrity: the data present on the DNS (associated with a domain name) must not be corrupted.
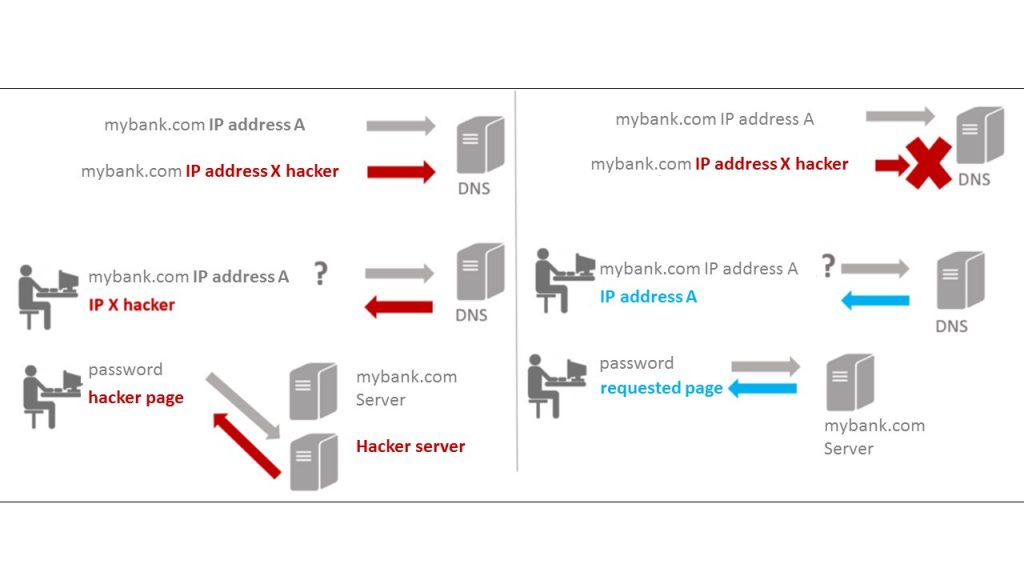
- Confidentiality: to protect the privacy of users, the DNS implements various solutions that increase the confidentiality of DNS requests. If the requests are not confidential, it is possible to analyze users’ browsing information.
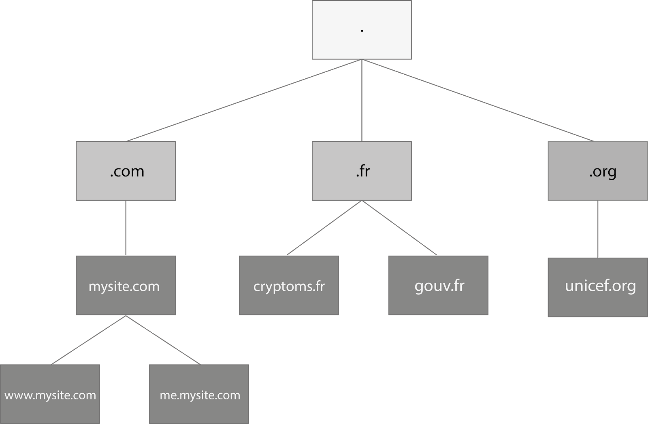
The domain name system is based on a centralized model of trust. It is distributed throughout the world and managed by different actors in a hierarchical manner, in several levels; a root level, a first level where extensions are managed by registries, then a second level managed by registrars. The whole thing is orchestrated by ICANN, the Internet’s regulatory authority.
For more than 30 years, many extensions and functionalities have been added to the DNS, which technically translates into an increase in the complexity of the infrastructure.
Blockchain technology could be a considerable evolution for DNS, bringing several advantages and new functionalities.
Blockchain and decentralized registry
A Blockchain is a data structure accessible to all and distributed over a decentralized network; the data is replicated on each node of the network, there is no central authority. Everyone has the possibility to read its contents, add data and even join the network. The concept was first implemented in 2009 with Bitcoin, but today there are many different Blockchain technologies, each with their own properties.
The data is entered on a Blockchain via transactions. The transactions are grouped into blocks, each block is then validated by the network and then brought together. Thus, a Blockchain contains the history of all the transactions carried out since its creation.
The validation rules are written in the Blockchain protocol, which each member of the network respects. To ensure compliance with its rules, the Blockchain protocols are based on consensus algorithms, the best known being the Proof of Work. These algorithms guarantee the integrity, immutability and security of the data on the Blockchain.
The Blockchain technology meets several DNS needs:
- Availability: a decentralized, peer-to-peer network cannot be stopped. It could replace or complement Anycast infrastructures.
- Integrity: the consensus protocol of a Blockchain guarantees, by nature, the integrity of the data. Furthermore, the data cannot be modified. These properties would eliminate the need for DNSSEC and its famous key renewal ceremony.
- Confidentiality: Requests made to read the Blockchain data can be encapsulated in an HTTPS channel in the same way as the DNS over HTTPS (DoH) protocol. There are few DoH resolvers today, so traffic is centralized around a limited number of actors. The use of a Blockchain would offer the possibility of querying any node on the network, thus limiting centralization and SPF (single point of failure).
The data included in the DNS zone files, i.e. the domain name configurations, could therefore be distributed on a Blockchain. Each player (registries, registrars) could directly interact with this Blockchain to manage the domain names. This is the idea of the DNS on Blockchain.
New needs
In recent years, with the emergence of Blockchain technologies, new means of values exchange have developed, particularly with tokenization, crypto-assets and decentralized applications (dapps); we talk about Web 3.0, or the Internet of Value.

Digital wallets and decentralized applications work with identifiers that are difficult to read, e.g. 0x483add28edbd9f83fb5db0289c7ed48c83f55982 for a wallet address.
Being able to associate this type of address with domain names, within a universal naming system, could be of real interest for tomorrow’s Web applications. It would be possible to have a wallet of crypto-assets or a decentralized application configured directly behind a domain name. This could also be useful for the digital identity of companies and their brands.
DNS on Blockchain, today
Many naming system projects on Blockchain are currently under development, each with an implementation of its own.
Some applications propose new domain names extensions (TLDs), such as .bit, .zil, .crypto, .eth, etc. This is particularly the case for Namecoin and UnstoppableDomains. These systems are completely independent of the traditional DNS and ICANN. Registration is managed directly by users, and names resolution is generally done through a browser extension. The Opera browser has recently natively integrated the resolution of these domain names.
These applications are functional and the names registration is not controlled. There are therefore many cases of cybersquatting. Users register names in the hope of reselling them and making a profit. This obviously poses a problem for trademark owners, and will certainly prevent the adoption of these solutions by companies.

Other projects propose complementary solutions to DNS. In particular, Ethereum Name Service (ENS) offers a names system on Blockchain that integrates with the traditional DNS. If you are the holder of a domain name and can prove it with a DNSSEC registration, you can then register this same name on the Blockchain service. This allows you to combine the advantages of traditional DNS and DNS on Blockchain.
The .kred, .xyz and .luxe extensions already support this integration on Blockchain, and ENS plans to propose it for all DNSSEC-compatible extensions. This project is quite promising, Ethereum Name Service has recently joined the DNS-OARC (DNS Operations, Analysis, and Research Center).
The Handshake project proposes a naming protocol to manage the root level of the DNS, and provide an alternative to certification authorities. It challenges the trust and governance model of the DNS to experiment with a more decentralized, secure and resilient system based on validation of DNS zones by participants in the network.
Conclusion
The DNS on Blockchain could be a considerable evolution of the DNS; it would bring several advantages and new functionalities thanks to the Blockchain technology, which would benefit the development of the decentralized web.
Today, however, there are still no technologies and applications on which there is unanimous agreement, even though many projects and PoC are under development. They are not yet mature enough to be used on a large scale. Improvements in terms of scalability, security and usability need to be made.
The collaboration of the Internet players (ICANN, DNS-OARC, registries) seems essential for a technology to reach consensus and be adopted, in particular to set common rules. This is a subject to be followed closely over the next few years.
Are you interested in blockchain and crypto-assets topics? Don’t hesitate to consult the website of our collaborator Steve Despres: https://cryptoms.fr/