In October 2016, many popular websites like Amazon, Twitter, Netflix and Spotify have become unavailable to millions web users in the United Sates, during almost 10 hours, i.e. an eternity. The cause, one of the most powerful attacks of Internet history on Dyn’s DNS services, a major actor in this sector.
Other companies like Google, The New York Times and many banks have also been the victims of different kinds of attacks aiming at the DNS, the last few years, and if in many companies, the DNS stays forgotten, things are evolving towards awareness forced by these many attacks.
Attack #1: DNS cache poisoning and spoofing
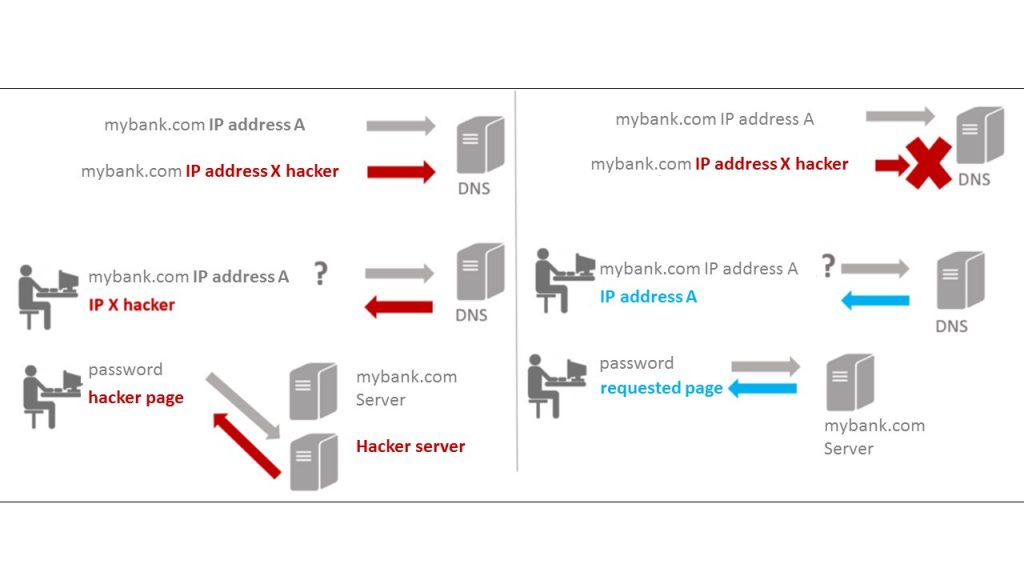
The aim of DNS poisoning is to take web users towards a scam website. For example, a user enters gmail.com in their web browser with the objective to consult their mailbox. The DNS having been poisoned, it’s not the gmail.com page which is displayed but a scam page chosen by the criminal, in order, for example, to retrieve the email box accesses. The users entering the correct domain name, will not see that the website they’re visiting is not the right one but a scam one.
It creates a perfect opportunity for the cybercriminals to use phishing methods in order to steal information, either identification information or credit card information from unsuspicious victims. The attack can be destructive, depending on many factors, the attacker’s intention and the DNS poisoning impact.
How are the hackers making their strike? By exploiting the DNS cache system.
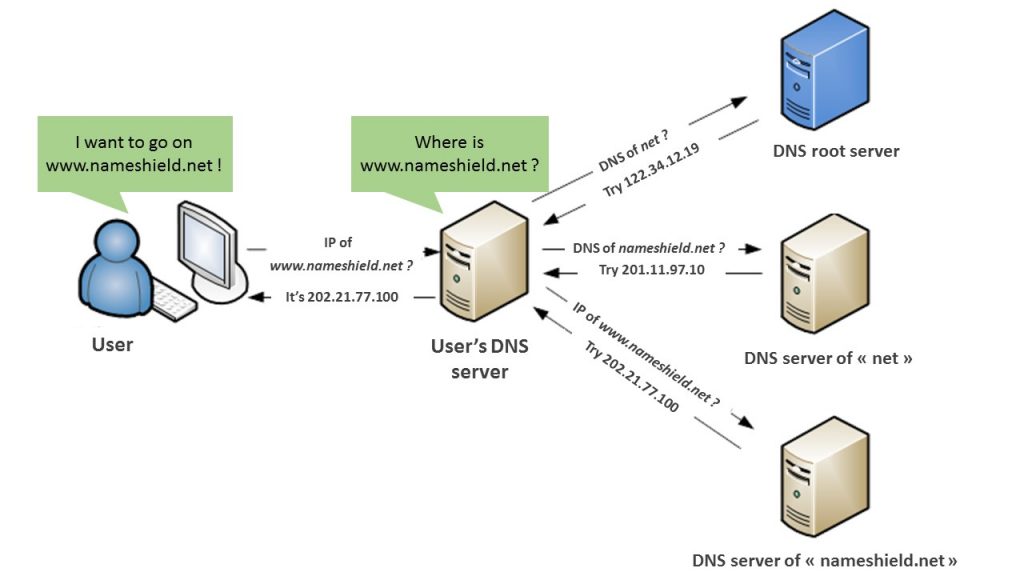
The DNS cache is used in all the web to accelerate the time charging and reduce the charges on DNS servers. The cache of a web document (web page, images) is used to reduce bandwidth consumption, the web server charge (tasks it carries out) or to improve the consultation speed of the browser use. A web cache keeps documents copies transiting through its way. Once a system requests to the DNS server and receives an answer, it records information in a local cache for a faster reference, in a given time, without having to search the information. The cache can answer to past requests based on its copies, without using the original web server.
This approach is used around the web in a regular way and in chain. The DNS server records are used to cache records on another DNS. This server is used to cache DNS records on network systems like rooters. These records are used to create caches on local machines.
DNS poisoning arrives when one of its caches is compromise.
For example, if a cache on a network rooter is compromised, then anyone who uses it can be misdirected towards a fraudulent website. The false records of DNS is branched to the DNS caches on the machine of each user.
This attack can also target the high links of the chain. For example, a major DNS server can be compromised. It can damage DNS servers’ caches managed by the Internet services providers. The “poison” can impact on the systems and peripheral networking of their customers, which allows to forward millions of persons towards fraudulent websites.
Does it seem crazy to you? In 2010, many American web users couldn’t access websites like Facebook and YouTube, because a DNS server of a high level internet services provider has accidently retrieved the records of the Chinese big firewall (Chinese Government blocked the accesses to these websites).
The antidote to this poison
The DNS cache poisoning is very difficult to detect. It can last until the TTL (time to live – validity time of a request in cache) expires on the cache data or an administrator realizes it and resolves the problem. Depending on the TTL duration, servers can take some days before resolving the problem by themselves.
The best methods to prevent an attack by DNS cache poisoning include the regular update of the program, the reduction of TTL times and the regular suppression of DNS caches of local machines and network systems.
For the registries that allow it, the implement of DNSSEC is the best solution in order to sign domain names’ zones on all the chain and make impossible a cache poisoning attack.
Attack #2: Attack by DNS amplification (of DDoS type)
Attacks by DNS amplification are not threats against DNS systems. Instead of this, they exploit the open nature of DNS services to reinforce the power of the attacks by distributed denial of services (DDoS). These attacks aren’t the lesser known, targeting for example well known websites like BBC, Microsoft, Sony…
Hold on and amplify
DDoS attacks generally occur with the help of a botnet. The attacker uses a network of computers infected by malwares to send mass traffic towards the target, like a server. The purpose is to surcharge the target and slow it or crash it.
Attacks by amplification add more power. Instead of directly sending traffic from a botnet to a victim, the botnet sends requests to other systems. These systems answer by sending more important traffic volume to the victim.
Attacks by DNS amplification are the perfect examples. The attackers use a botnet to send thousands of search requests to open DNS servers. The requests have a fake source address and are set up to maximize data quantity sent back by each DNS server.
The result: an attacker sends relatively restrained quantities of traffic from a botnet and generates traffic volumes proportionally superior or “amplified” of DNS servers. The amplified traffic is directed towards a victim which causes the system’s breakdown.
Detect and defend ourselves
Some firewalls can be set up to recognize and stop the DDoS attacks as they occur by deleting artificial packages trying to flood the systems on the network.
Another way to fight against these DDoS attacks consists in hosting your architecture on many servers. This way, if a server is surcharged, another one will always be available. If the attack is weak, the IP addresses of traffic sending can be blocked. Furthermore, a rise of the server’s bandwidth can allow it to absorb an attack.
Many dedicated solutions also exist, conceived exclusively to fight against DDoS attacks.
Attack #3: DDoS attack on DNS
DDoS attacks can be used against many systems types. It includes the DNS server. A successful DDoS attack against DNS server can cause a breakdown, which makes the users unable to surf the web. (Note: users are susceptible to continue to reach websites they have recently visited, by supposing that the DNS record is registered in a local cache.)
This is what happened to Dyn’s DNS services, as described at the beginning of this article. The DDoS attack has surcharged the DNS infrastructures that prevents millions of persons to access principal websites which domain names were hosted on.
How to defend yourself against these attacks? It all depends on your DNS configuration.
For example, do you host your DNS server? In this case, there exist measures that you can take to protect it, by updating the last patches and by only allowing local computers to access it.
Are you perhaps trying to reach the attacked DNS server? In this case, it will probably be hard for you to connect. That’s why, it’s wise to set up your systems to rely on more than one DNS server. This way, if the principal server doesn’t answer anymore, a backup server will be available.
Predict and reduce the attacks
DNS server attacks are a major risk of security for the network and have to be taken seriously. Companies, hosts and Internet services providers, implement backup measures to prevent and reduce the effects of this kind of attacks when they are the victims.
Following these attacks, ICANN has highlighted more strongly than ever the necessity to use the DNSSEC protocol to sign each DNS request with a certified signature, by ensuring that way the authenticity. This technology’s disadvantage is that it has to be implemented at every stages of DNS protocol in order to operate properly – which arrives slowly but surely.
Opt for hosted infrastructures and maintained by DNS experts. Make sure that the network is anycast (multiple points of presence distributed around the world or at least on your influence zones), beneficiates of anti-DDoS filter and offers you supplementary security solutions like DNSSEC but also failover, to integrate the DNS in your PCA and PRA.
Nameshield has its own DNS Premium infrastructure to answer to their customers’ needs. This infrastructure answers in particular to (even exceeds) all ANSSI prerequisites. The DNS Premium solution is integrated in the scope of our ISO 27001 certification.
Don’t hesitate to contact us for all questions regarding cyberattacks.




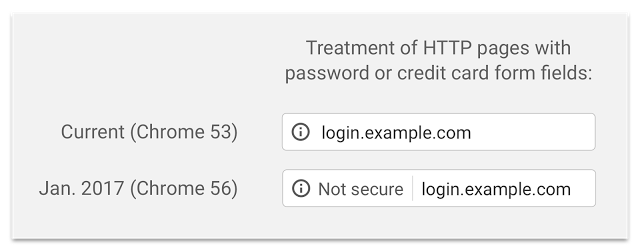
 Chrome 53 launched on 31 August 2016 and with it Google is continuing its offensive for a safer internet.
Chrome 53 launched on 31 August 2016 and with it Google is continuing its offensive for a safer internet.