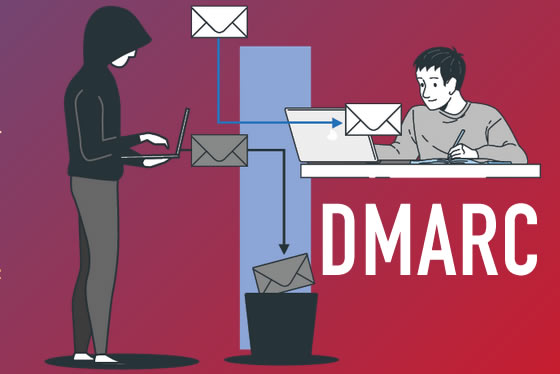
Google and Yahoo recently announced significant changes to their e-mails authentication requirements. The aim of these adjustments is to strengthen the security of online communications, a major issue in the current context of cybercrime.
The two giants are emphasizing the adoption of advanced authentication protocols, in particular DMARC (Domain-based Message Authentication, Reporting, and Conformance). DMARC relies on the existing SPF and DKIM standards, providing a robust method for verifying e-mails’ authenticity and reducing the risk of identity theft and phishing.
To implement these new requirements, Google and Yahoo will adjust their algorithms to give priority to e-mails from domains that have correctly implemented DMARC. The aim of this measure is to improve the deliverability of authenticated e-mails, reinforcing users’ trust in the security of their e-mail inboxes.
The new guidelines will apply from February 1, 2024 to all senders who send more than 5,000 emails per day. They underline Google and Yahoo’s commitment to fight against online threats, in particular phishing, a common method used by cybercriminals to deceive users and gain access to their sensitive information. By adopting stricter e-mails authentication requirements, these companies are strengthening users’ protection against malicious attacks.
It is now essential for domains holders and players in the digital world to comply with these new guidelines, in order to contribute to the creation of a safer and more secure Internet for all.
Nameshield’s experts are at your disposal to assist you in deploying this protocol.